- Access Security Monitor
- Add Your Website to Security Monitor
- Set Default Notification Email
- Different Notification Email for Each website
- New Security Monitor Report
- Remove Website from Security Monitor
- Website Security Report Details
- A path is visible. Brute Force attack is imminent!
- WordPress XML-RPC Brute Force exploit detected!
- WordPress path is still accessible!
- WordPress readme.html is accessible!
- WordPress old paths are visible in the source code!
- WordPress Prefetch https://s.w.org is visible!
- WordPress https://api.w.org/ is visible!
- WordPress “Powered by WordPress” is visible!
- Run New Security Report
- Export Security Report
Websites change constantly. So, when it comes to security, the moment you stop monitoring your site, you expose it to significant risk.
WP Ghost ensures that your site’s security monitoring is continuous through the Security Monitor feature.
Once you add a site connected to your account to Security Monitor, WP Ghost will scan it for security issues every week.
If there is any security issue with the website, it will be documented in a dedicated website security report, and the report will be conveniently sent to your preferred email address.
This makes it easy to keep track over site’s security and fix potential security issues.
The Security Monitor feature supplements the Security Check feature. Both features scan your WordPress site for similar issues and WordPress-specific vulnerabilities that affect its security.
Access Security Monitor
The Security Monitor feature is located within your WP Ghost Dashboard account in the Security Monitor section.

For every website in the security monitor list, you’ll see the following information:
- The URL (website) for which the report has been generated.
- Whether the option Email Notification has been enabled or not.
- The date when the website has been added to Security Monitor (Created At column).
- The date when the website was last verified (Last Verified column).
Add Your Website to Security Monitor
To add the website you want to monitor and generate reports for, click on the +New button shown in the screenshot below.
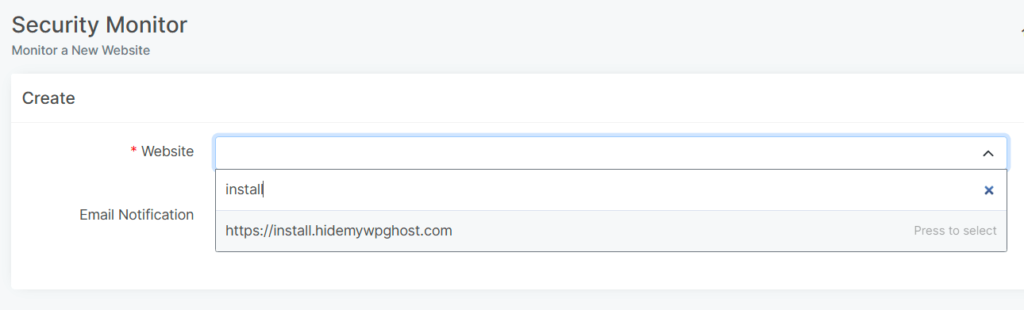
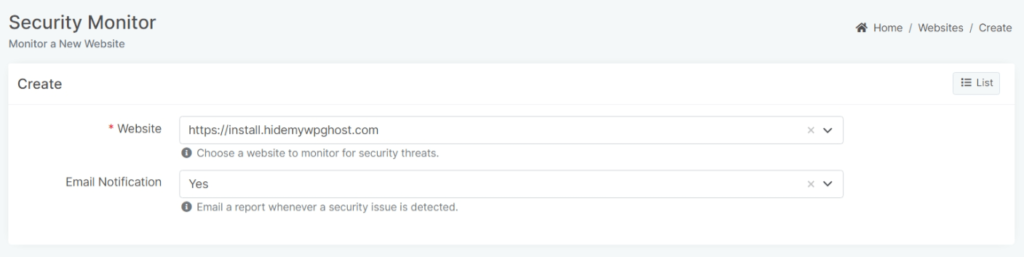
Clicking on the +New button will take you to a new panel where you can:
- Add a new website for which you want WP Ghost to generate a security report. Once you connect a website to your account on the WP Ghost plugin installation, the website will appear in the security monitor websites list, and you can simply add the website to the security monitor.
- Choose whether to receive a email notification containing the report via email or not.
Set Default Notification Email
- Go to your Profile > Settings section.
- Specify the Default Notification Email address where you want to receive the report.

Note! The email address you set here is also where you’ll receive the User Events Email Alerts.
Different Notification Email for Each website
You can also set up an individual email address for each website you’ve added to Security Monitor (useful for cases when you want each Website Report to be sent to different email addresses).
- Go to the Connected Sites section.
- Click on the pencil from the Alert Email column to add an email address.
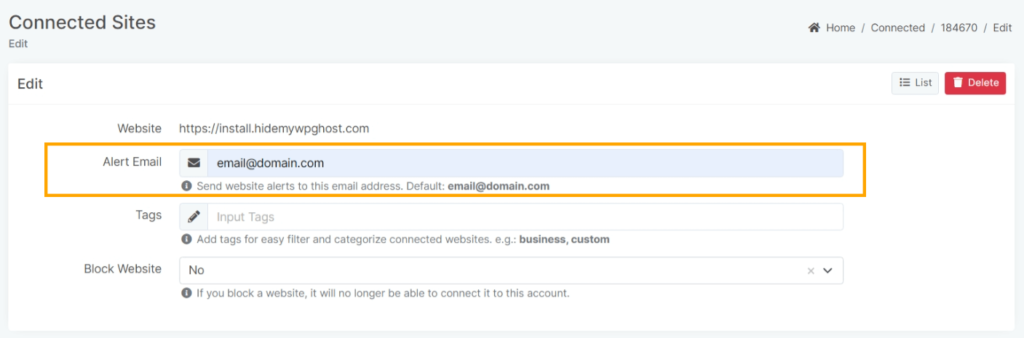
The settings you make here have priority over those you may have made in Profile > Settings section .
Note! If no email address is specified in either the Profile > Settings section or the Connected Sites section, WP Ghost will send the weekly website report to the email address connected to your account.
New Security Monitor Report
Once you’ve added your website to Security Monitor, you can access the WP Ghost security report for your website from the Security Monitor section.
- Go to the Security Monitor section.
- Click on the View Report link for the website you want to check the security report.
Remove Website from Security Monitor
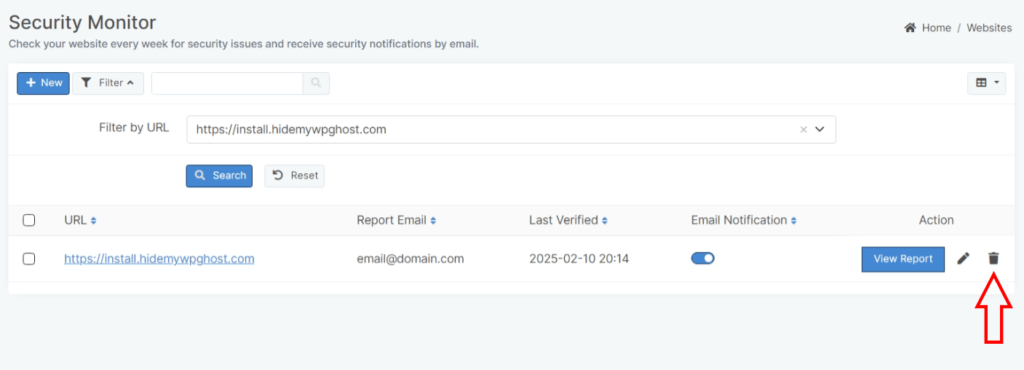
To remove a website from Security Monitor, follow these steps:
- Go to the Security Monitor section.
- Click on the Trash icon for the website you want to remove from the Security Monitor.
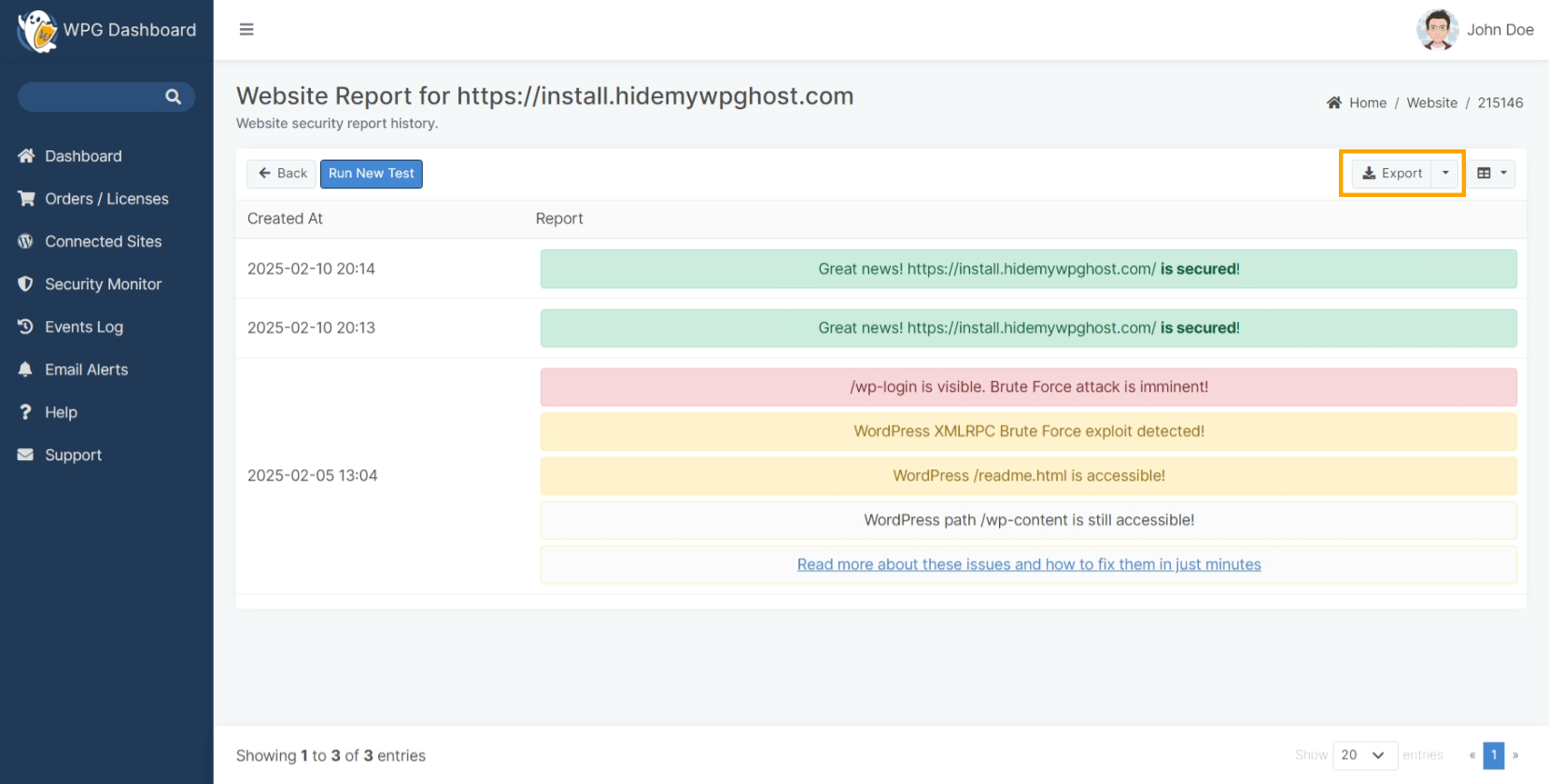
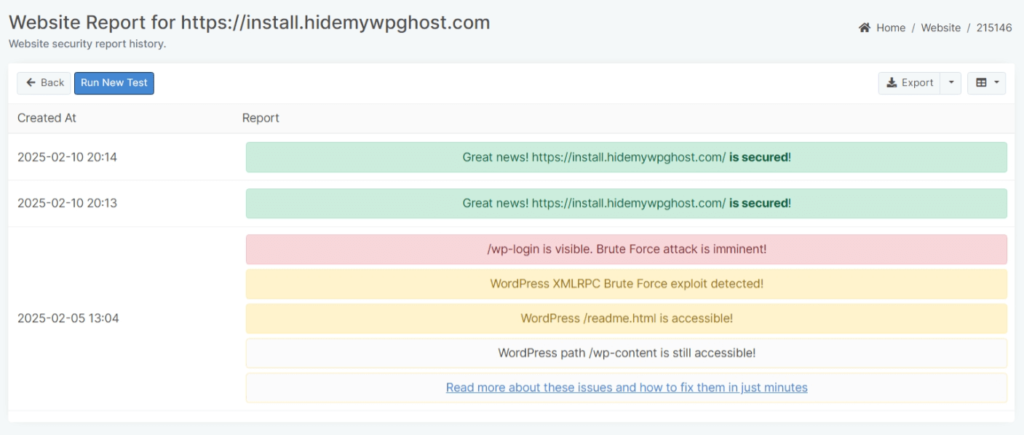
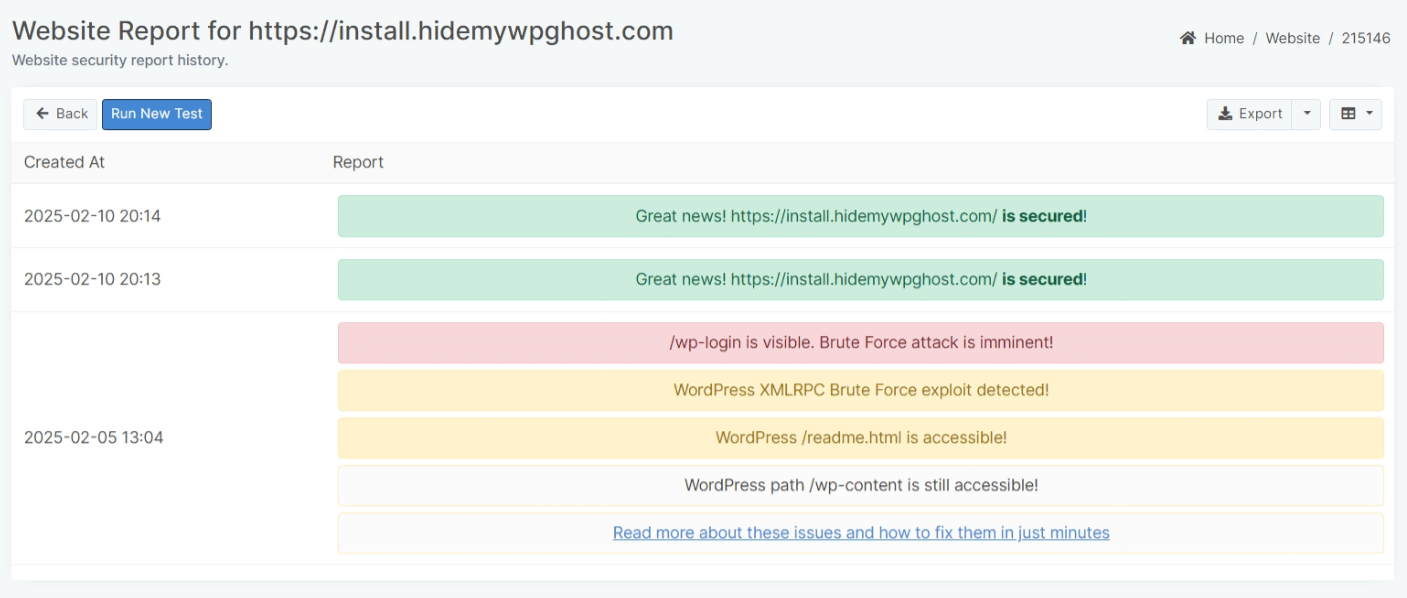
Website Security Report Details
The Website Report contains security insights WP Ghost uncovered after scanning a specific website you added to the Security Monitor.
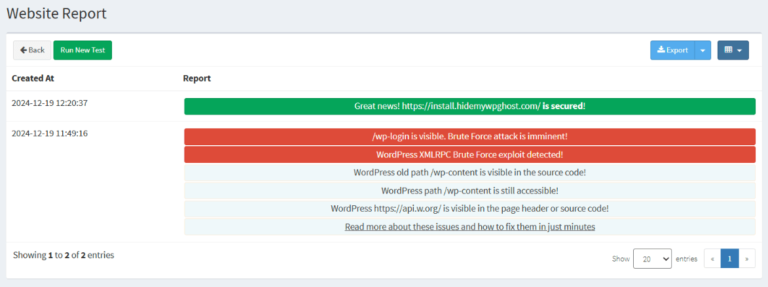
In the screenshot below, you can see an example of how a website report looks like.
- The Blue Notification is used for report insights that are purely informative (they don’t necessarily require you to take action)
- The Red Notification is used to highlight critical issues that you still need to resolve to address WordPress vulnerabilities and strengthen your website’s security.

Next up, we’ll go over every individual type of warning that WP Ghost may generate and display inside the Website Report for a site connected to your account.
We’ll explain what each of them means and how to address them using WP Ghost features, so let’s get to it.
A path is visible. Brute Force attack is imminent!

This means that WP Ghost found a vulnerable WordPress authentication path which hackers could exploit in order to perform brute force login attempts.
The best solution is to change and hide the wp-login and wp-admin paths from hacker bots.
You can also activate Brute Force Protection using Google reCaptcha or Math reCaptcha .
👍 Learn how to do this: Change and Hide wp-login Path
WordPress XML-RPC Brute Force exploit detected!
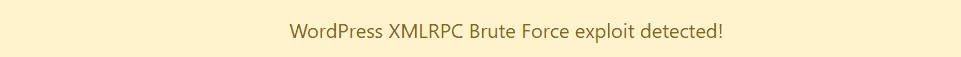
XML-RPC could open your site to various attacks and lead to other security issues. This feature is not used anymore because WordPress is now using API which is much safer.
If you are using other types of servers, the best solution is to restrict access to the /xmlrpc.php file through .htaccess or the server config file.
👍 Learn how to do this: Disable XML-RPC Access
WordPress path is still accessible!

This means the WordPress common paths wp-content/plugins and wp-content/themes are still accessible. Since most attacks are made on vulnerable plugins and themes, it’s crucial to hide them and prevent hackers from accessing the vulnerable files.
You can hide the WordPress Common paths very easily by changing and hiding them with WP Ghost.
👍 Learn how to do this: Change and Hide wp-content Path
WordPress readme.html is accessible!
Some of the root files like readme.html, license.txt, wp-config.php contain information about your WordPress version, Database username and password, paths, and server details.
These files allow hackers to know all about your Content Management System and server without even entering your website – and are often the first files that hacker bots access.
It’s important to restrict access to all these files, as it helps you stop a lot of attacks and prevent unnecessary server traffic.
👍 Learn how to do this: Hide WordPress Common Files
WordPress old paths are visible in the source code!
This means that wp-content/plugins, wp-content/themes, /wp-admin, and other common paths are visible in your website’s source code. Hacker bots will usually crawl your website to get information about your themes and plugins.
The best way to prevent this is to customize the paths and even the plugins’ and themes’ names.
This will stop most attacks on your installed plugins and themes. After you change the paths, you can hide the old paths for enhanced WordPress security.
👍 Learn how to do this: Hide WordPress Common Paths
WordPress Prefetch https://s.w.org is visible!
This META is mostly added by WordPress for the emoji feature.
But this META lets hackers know that you’re using WordPress as your Content Management system. As a result, bots will initiate more attacks on your site in order to find breaches and vulnerabilities they can exploit.
👍 Learn how to do this: Hide WordPress DNS Prefetch
WordPress https://api.w.org/ is visible!

api.w.org is used for WordPress REST API discovery. This is mostly used by developers, so it’s not needed in your source code.
This link tells hackers that you have a WordPress website. As a result, bots will initiate more attacks to find breaches they can exploit to gain access to your site.
👍 Learn how to do this: Hide WordPress Generator
WordPress “Powered by WordPress” is visible!

Allowing this text is the equivalent of shouting that you’re using WordPress as your CMS in a room full of hackers.
Usually, basic mistakes like these can lead to some pretty serious consequences. The good news is you can typically easily remove this text, as most themes already have the option for removing the “Powered by WordPress” copy. Go to the theme’s settings or Admin panel > Appearance > Customize, and if the theme you’re using features this option, you will find it in one of these two places.
Note! Remember to customize the Tagline in Settings > General. The default WordPress tagline that sites get when they are created is “Just another WordPress site”, which also acts as a huge announcement, letting the world (including hackers) know that you have a WordPress website.
Run New Security Report
These are some of the most common vulnerability issues hackers typically exploit to access a WordPress site.
Make sure to also run a local Security Check to get a full security report about your website and uncover urgent security threats that expose your site to different types of attacks.
You can always run a new test and refresh the information for your website by clicking on the Run New Test button shown in the screenshot below.
By doing this, WP Ghost will run a new check of your website and deliver the latest security insights it uncovered for that particular site inside the Website Report Panel.
Export Security Report
You can export a Website Report using the Export button on the right of the screen at any time.