One common WordPress security concern involves using XML-RPC, a feature that allows developers to perform various actions on your site.
However, it can also be exploited for malicious purposes, such as brute force attacks. This tutorial will walk you through disabling access to xmlrpc.php in WordPress using the WP Ghost plugin.
What is XML-RPC in WordPress?

XML-RPC (XML Remote Procedure Call) in WordPress is a protocol that allows remote communication between different software applications.
It enables developers to interact with a WordPress website from a distance, typically using API (Application Programming Interface) calls encoded in XML format.
Although XML-RPC is not widely used anymore, the following is a list of its functionalities in WordPress:
- Remote access: XML-RPC allows external applications, services, and websites to perform various actions on a WordPress site without directly accessing its admin interface. This allows for remote management and integration with third-party software.
- Functionality: XML-RPC can perform a wide range of tasks, such as publishing and editing posts, retrieving site information, managing comments, and even performing administrative actions like updating plugins and themes.
- Automation: Developers often use XML-RPC to automate tasks like content publishing, data synchronization, and managing multiple WordPress sites from a single interface.
Why is it Essential to Secure the XML-RPC path?
Security is crucial regarding XML-RPC in WordPress because, if not properly managed, it can pose serious risks to your website.
- Brute Force Attacks: Attackers often use XML-RPC to launch brute force attacks. Imagine someone trying every possible key to unlock your front door. They do this by repeatedly sending login attempts through XML-RPC until they guess the correct credentials.
- DDoS Attacks: XML-RPC can be exploited to initiate Distributed Denial of Service (DDoS) attacks. This is like an army of robots overwhelming your fortress, making your website inaccessible to legitimate visitors.
- Content Injection: If an attacker gains access through XML-RPC, they might inject malicious code or spam content onto your website, damaging your brand’s reputation and potentially infecting your visitors’ devices.
- Resource Drain: XML-RPC can be used to perform resource-intensive tasks, consuming your server’s resources and slowing down your website’s performance.
However, while XML-RPC offers many benefits for developers, it has also been a target for security concerns. Because it allows remote access to a WordPress site, it can potentially be exploited by hacker bots for brute force attacks.
To address these security issues, some users choose to disable XML-RPC access, especially if they don’t require remote functionality or use alternative methods for remote interactions with their WordPress sites.
How to Secure XML-RPC with WP Ghost
Activate Safe Mode or Ghost Mode
- Select Safe Mode or Ghost Mode. Safe Mode provides basic protection, while Ghost Mode offers more advanced security features.

Disable XML-RPC Access
- Go to WP Ghost > Change Paths > API Security.
- Switch on the option Disable XML-RPC access to disable the access to the xmlrpc.php path.
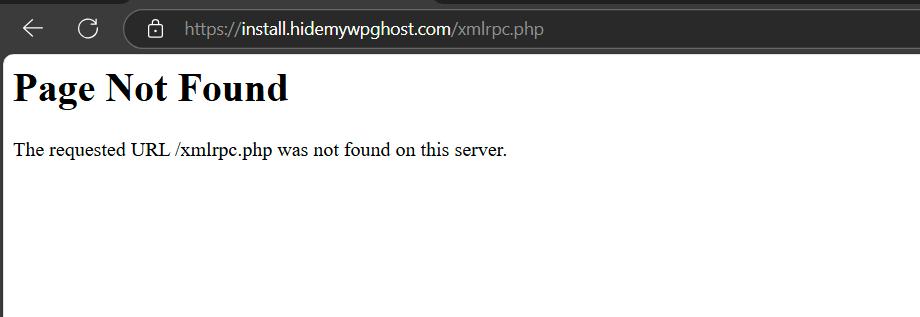
Disabling XML-RPC access effectively prevents direct access to the xmlrpc.php file, making it inaccessible to potential attackers.

Plugins Compatibility
To hide the XML-RPC from hackers but let Jetpack IPs access the website, add this code in .htaccess at the beginning of the file:
<Files xmlrpc.php> Order deny,allow Deny from all Allow from 127.0.0.1 Allow from *.wordpress.com Allow from 192.0.64.0/18 Allow from 185.64.140.0/22 Allow from 2a04:fa80::/29 Allow from 76.74.255.0/22 Allow from 192.0.65.0/22 Allow from 192.0.80.0/22 Allow from 192.0.96.0/22 Allow from 192.0.123.0/22 Satisfy All ErrorDocument 404 / </Files>
Now, whenever someone tries to directly access xmlrpc.php, they’ll see the 404 page not found error.
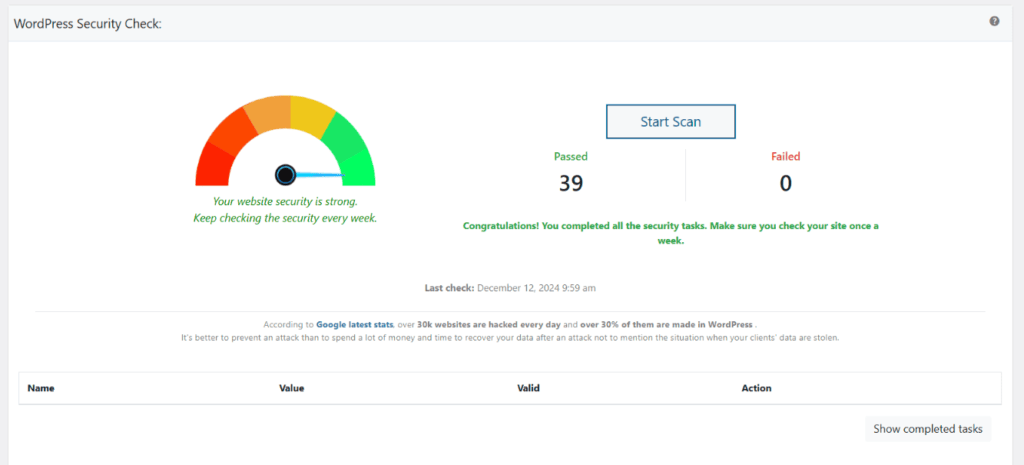
Run a Security Check
After saving your changes, it’s important to run a security check to verify that the path is hidden and secured.
Troubleshooting
JetPack Plugin Analytics not Working with Disabled XML-RPC Access
If disabling XML-RPC in WP Ghost causes JetPack analytics to stop working, a simpler solution is to whitelist JetPack’s IP addresses in WP Ghost’s firewall. This ensures JetPack can communicate with WordPress.com securely without fully re-enabling XML-RPC access.
Verify JetPack Errors
Check your JetPack dashboard or WordPress admin for error messages like “Error connecting to WordPress.com” or “Stats not available“.
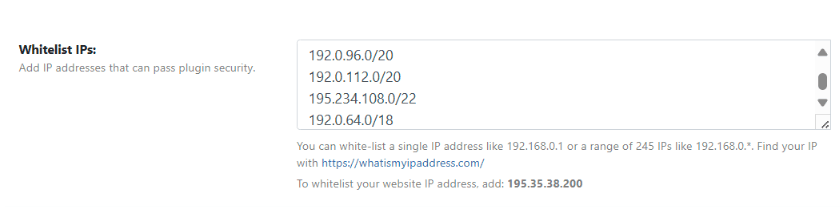
Whitelist JetPack IPs
JetPack uses specific IP ranges to communicate with WordPress.com. For the latest IP addresses, visit JetPack’s official IP documentation.
Re-enable XML-RPC Access
To ensure JetPack works, a solution is to allow XML-RPC access temporarily.
- Go to WP Ghost > Change Paths > API Security.
- Switch Off the option Disable XML-RPC access to allow the access to the xmlrpc.php path.
Test JetPack Connection
Go to JetPack > Dashboard and reconnect your site to WordPress.com if needed. Check if analytics data is being updated correctly.
This approach provides a balanced solution: you maintain the security of WP Ghost while ensuring JetPack analytics work seamlessly.
