What are Security Headers?

Security headers are directives included in the HTTP responses from web servers that instruct the web browser on how to handle the content of a web page.
These headers help protect web applications from various security threats by mitigating risks associated with cross-site scripting (XSS), cross-site request forgery (CSRF), clickjacking, and other common vulnerabilities.
By setting security policies at the browser level, these headers provide an additional layer of defense against potential attacks.
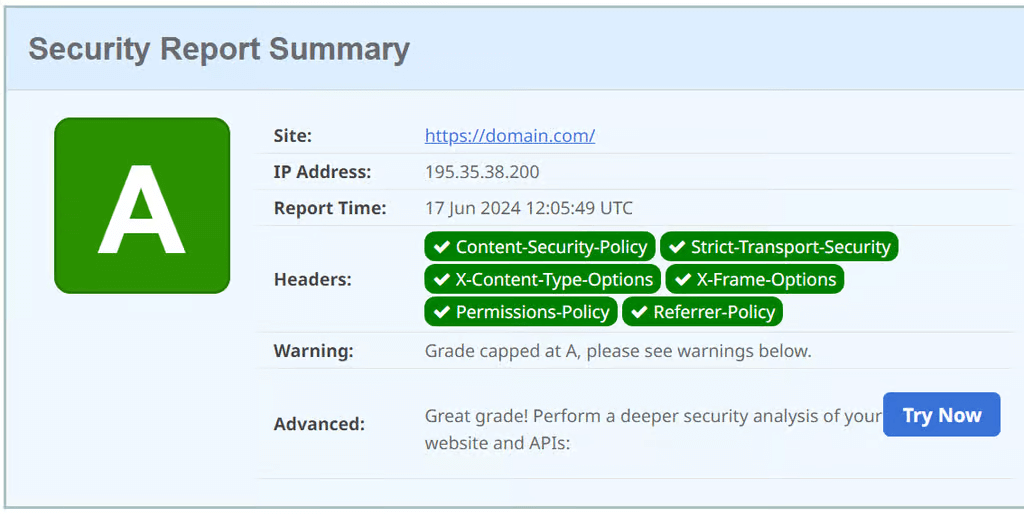
How to Use Security Headers in WP Ghost
Activate Header Security
To activate this feature:
- Go to WP Ghost > Overview or WP Ghost > Firewall > Header Security.
- Switch on the Add Security Headers for XSS and Code Injection Attacks option.
Setting Recommended Security HTTP Headers in OpenLiteSpeed:
https://amireslampanah.com/2020/09/setting-recommended-security-http-headers-in-openlitespeed/

When activated, WP Ghost implements essential headers through the configuration file and PHP, providing both functionality and enhanced security. This adds an extra defense layer against various attack types, such as Cross-Site Scripting (XSS).
Here are the security headers you can add:
Strict-Transport-Security (HSTS)
The Strict-Transport-Security (HSTS) header ensures that a web application is accessed only over HTTPS, preventing man-in-the-middle attacks and cookie hijacking. more details >>
Implementation
To implement HSTS, add the following header to your HTTP response:
Strict-Transport-Security: max-age=31536000; includeSubDomains; preloadDetails
max-age=31536000: Specifies the duration (in seconds) that the browser should remember to only access the site via HTTPS.includeSubDomains: Applies the rule to all subdomains.preload: Requests inclusion in the HSTS preload list, a list of sites hardcoded into browsers as HTTPS-only.
Content-Security-Policy (CSP)
The Content-Security-Policy (CSP) header helps prevent cross-site scripting (XSS), clickjacking, and other code injection attacks by specifying which sources of content are allowed to be loaded on the site. more details >>
Implementation
A typical CSP header might look like this:
Content-Security-Policy: default-src 'self'; script-src 'self' https://apis.google.comDetails
default-src 'self': Only allows resources from the site’s own origin.script-src 'self' https://apis.google.com: Allows scripts from the site’s own origin and Google’s APIs.
X-Frame-Options
The X-Frame-Options header prevents clickjacking attacks by controlling whether a browser should be allowed to render a page in a <frame>, <iframe>, <embed>, or <object>. more details >>
Implementation
To implement, add one of the following headers:
X-Frame-Options: DENYor
X-Frame-Options: SAMEORIGINDetails
DENY: Prevents the page from being framed.SAMEORIGIN: Allows framing only by the same origin
X-XSS-Protection
The X-XSS-Protection header enables the cross-site scripting (XSS) filter built into most modern web browsers, providing a basic level of protection against XSS attacks. more details >>
Implementation
Add the following header:
X-XSS-Protection: 1; mode=blockDetails
1: Enables the XSS filter.mode=block: Instructs the browser to block the page if an XSS attack is detected.
X-Content-Type-Options
The X-Content-Type-Options header prevents browsers from interpreting files as a different MIME type than what is specified, which can help mitigate drive-by download attacks. more details >>
Implementation
Add the following header:
X-Content-Type-Options: nosniffDetails
nosniff: Ensures the browser adheres to the MIME types specified in the Content-Type headers.
Cross-Origin-Embedder-Policy (COEP)
The Cross-Origin-Embedder-Policy header ensures that a document can only load resources that explicitly grant permission, enhancing the security of embedded content. more details >>
Implementation
Add the following header:
Cross-Origin-Embedder-Policy: require-corpDetails
require-corp: Requires cross-origin resources to explicitly grant permission using theCross-Origin-Resource-Policyheader.
Cross-Origin-Opener-Policy (COOP)
The Cross-Origin-Opener-Policy header helps protect against cross-origin attacks, such as cross-origin information leaks, by ensuring that a top-level document does not share a browsing context group with cross-origin documents. more details >>
Implementation
Add the following header:
Cross-Origin-Opener-Policy: same-originDetails
same-origin: Ensures the document is isolated from other origins, reducing the risk of cross-origin attacks.
Regularly reviewing and updating these headers in response to new security threats is also crucial in maintaining robust security.
