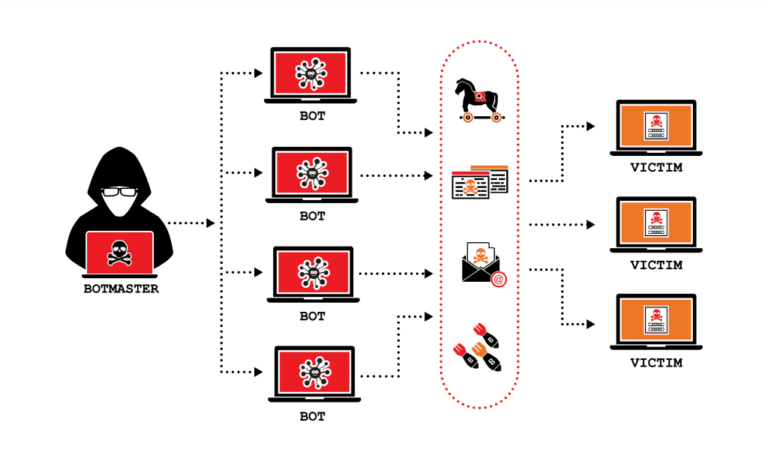
From one website to another, hacker bots load all the hacking URLs and queries without checking whether a website has a WordPress CMS. Once the bot gets a signal that a breach was found, it will automatically do a file inclusion exploit, inject malicious scripts and codes, and after that … well … is not bright.
As most attacks are made by bots rather than human hackers, each website can receive hundreds of calls per second, and the owner may not even know about it.

Hack URLs and Queries
I will resume the actions and the URLs to the WordPress CMS to keep it simple.
As most plugin and theme owners are not familiar with the types of bot attacks, they offer their work with small windows for hackers to find usernames and passwords, upload files on the server, inject scripts in files, and the list can continue.
For websites like WordPress, most of the attacks contain paths to /wp-content/plugins/ and /wp-content/themes/, as well as to the default /wp-login.php and /wp-admin.
As you can’t guarantee that all the plugins you have installed are secured or that an update will not cause a breach, I can say that it’s a lottery, and it’s a matter of time until a bot finds a breach.
Brute Force on Login
Hacker bots repeatedly attempt to guess login credentials using default CMS paths.
The default login path from WordPress wp-login.php is on the list of Brute Force attacks for every website. Hacker bots will access the login path and post different values for the user and password fields.
The attempts will start with the “admin” and “administrator” usernames and common passwords.
Hacker bots are ultra-fast computers. On a basic setup, a single bot can send anywhere from 10 to 100 requests per second. A botnet (network of compromised devices) can distribute attacks, exponentially increasing the number of attempts. If your server is fast and lacks protections, the rate can climb to 50–200 attempts per second.
Default Brute Force URLs:
https://demo.com/wp-login.php
https://demo.com/wp-admin/
Attempt Example:
POST requests with guessed usernames like “admin“, “administrator“, and passwords like “123456”, “password”, “qwerty123”, etc.
Usually, a bot can hack an unprotected website in just 5 minutes. Once your website is hacked, you will not always know because the bot will silently inject files in random directories and use your website for phishing or emailing.
SQL Injection Attacks
Bots inject malicious SQL queries into vulnerable forms or URLs to access or manipulate the database.
Example of queries:
https://demo.com/wp-content/plugins/vulnerable-plugin?id=1' UNION SELECT username, password FROM wp_users --
https://demo.com/?id=1'; DROP TABLE wp_users; --

These kinds of calls are made on all websites a bot will access, regardless of the CMS type. This is why it’s important to hide the CMS common paths to protect vulnerable plugins and themes.
File Inclusion Exploits
The file inclusion exploits attack is similar to the directory traversal attack, in which bots try to load malicious files by exploiting poorly coded plugins or themes.
Once the hacker bot manages to hack a website, it injects malicious code into the website and compromises it.
Example of queries:
https://demo.com/wp-content/themes/vulnerable-theme/?file=../../wp-config.php
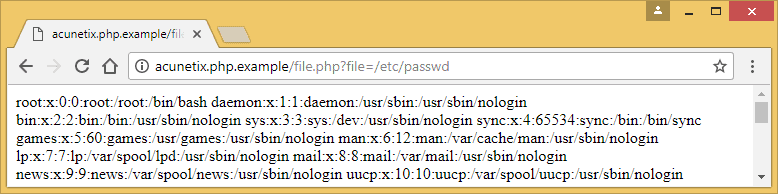
https://demo.com/wp-admin/admin-ajax.php?action=load_file&file=../../../../etc/passwd
https://demo.com/wp-content/uploads/../../wp-config.php
https://demo.com/wp-content/plugins/../themes/../../index.php
Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) is a type of web security vulnerability where attackers inject malicious scripts into webpages that are viewed by other users.
These scripts can steal sensitive information, hijack sessions, or perform unauthorized actions on behalf of the user.
Example of queries:
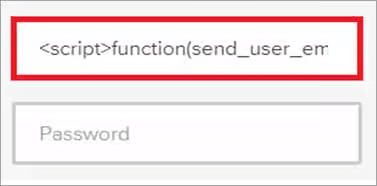
https://demo.com/?search=<script>alert('Hacked!')</script>
https://demo.com/wp-comments-post.php?name=<img src=x onerror=alert('XSS')>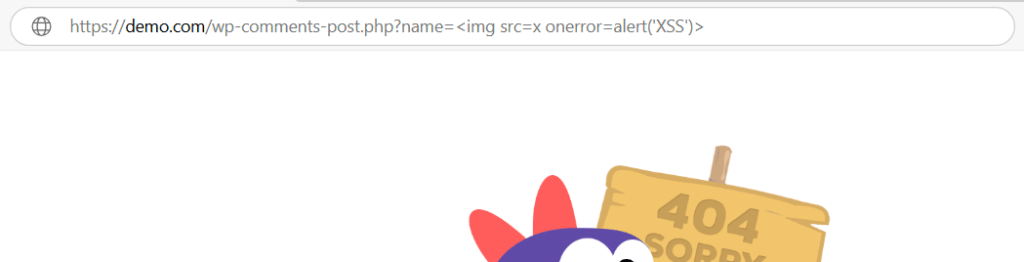
WordPress Files Exploits
Admin-Ajax Exploits
Hackers abuse the admin-ajax.php endpoint to perform unauthorized actions.
Example of queries:
https://demo.com/wp-admin/admin-ajax.php?action=upload_file&file=malicious.php
https://demo.com/wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php
Plugin and Theme Exploits
Bots exploit known vulnerabilities in outdated or poorly coded plugins/themes.
Example of queries:
https://demo.com/wp-content/plugins/vulnerable-plugin/exploit.php
https://demo.com/wp-content/themes/vulnerable-theme/lib/exploit.php
https://demo.com/index.php?page_id=45&file=../../../../wp-config.php
https://demo.com/wp-content/plugins/plugin-name/admin.php?page=options&cmd=rm+-rf+/*
https://demo.com/wp-json/wp/v2/users/1?_fields=id,name,slugXML-RPC path Exploits
Bots use xmlrpc.php to perform mass brute-force or DDoS attacks.
Example of queries:
https://demo.com/xmlrpc.php?<methodCall><methodName>system.multicall</methodName>Rest API Exploits
Bots use REST API wp-json to get the list of users.
Example of queries:
https://demo.com/wp-json/wp/v2/usersWP Ghost Protects Against These Attacks
- Path Protection: Hides and secure all common WordPress paths and files.
- Plugins and Themes Protection: Hides and secure all plugin and theme paths.
- SQL Injection Prevention: Blocks suspicious database queries.
- Brute Force Protection: Limits login attempts and adds reCAPTCHA.
- File Inclusion Blocking: Secures core, plugin and theme paths.
- XSS Defense: Filters and sanitizes input to block scripts.
Read more about WP Ghost: What is WP Ghost?